Unveiling the Power of Network TAPs and Packet Brokers
Posted by Admin on 2023 Oct 31st
In the realm of modern networking, the need for seamless access to network traffic and robust monitoring is undeniable. However, this requirement often clashes with the challenges of maintaining network performance, ensuring complete visibility, and scaling the infrastructure. To tackle these issues, Network TAPs and Network Packet Brokers (NPBs) come to the rescue.
Challenge 1: Non-Intrusive Access to Network Traffic
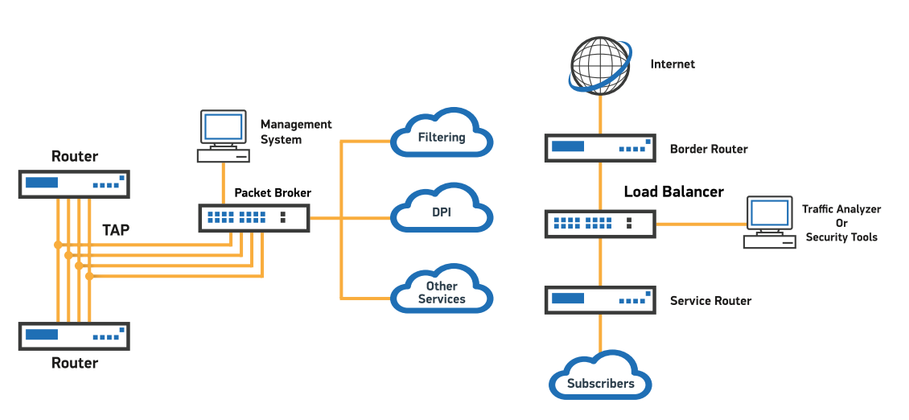
Accessing network traffic is vital, but traditional methods like SPAN ports can disrupt network performance. Network TAPs offer a solution. They passively copy traffic without causing congestion or failure. Your network's performance remains unscathed while TAPs ensure all packets are captured.
Challenge 2: Achieving 100% Visibility
Effective monitoring requires 100% visibility at line rate. Network Packet Brokers (NPBs) are the answer. NPBs aggregate, filter, and distribute traffic to multiple monitoring tools simultaneously. They ensure that relevant data reaches each tool efficiently, guaranteeing complete visibility without overwhelming resources.
Challenge 3: Scaling Without Complicating the Network
As networks expand, adding more monitoring tools can seem complex. NPBs simplify this process. They facilitate easy scaling without altering the network structure, ensuring your monitoring capabilities grow alongside your network.
Challenge 4: Lower total cost of ownership (TCO)
The Disaggregated Open Packet Broker Approach combines disaggregation and open standards, offering flexibility in hardware and software selection.. By separating hardware from software, disaggregated packet brokers often lead to cost savings. You can choose cost-efficient hardware components and avoid proprietary hardware vendor lock-ins.
In a nutshell, Network TAPs, NPBs, and the Disaggregated Open Packet Broker approach address the challenges of accessing network traffic, ensuring complete visibility, and scaling the infrastructure without introducing complexity. They are indispensable tools for optimizing network operations, enhancing security, and making informed decisions in our increasingly intricate network landscapes.